

SentinelOne Singularity™ Identity: Fortifying Active Directory Security with Real-Time Defense
In the age of relentless cyber threats, protecting sensitive identity assets within Active Directory is a paramount concern. SentinelOne's Singularity™ Identity emerges as a powerful solution that not only defends against credential misuse but also offers real-time infrastructure defense for Active Directory, Azure AD Domain Controllers, and domain-joined assets. Let's explore how this innovative platform is reshaping identity security.
Will Your Active Directory Withstand Direct Attack?

Singularity Identity is designed to defend Active Directory, Azure AD Domain Controllers, and domain-joined assets from adversaries aiming to gain privilege and move covertly within your network.
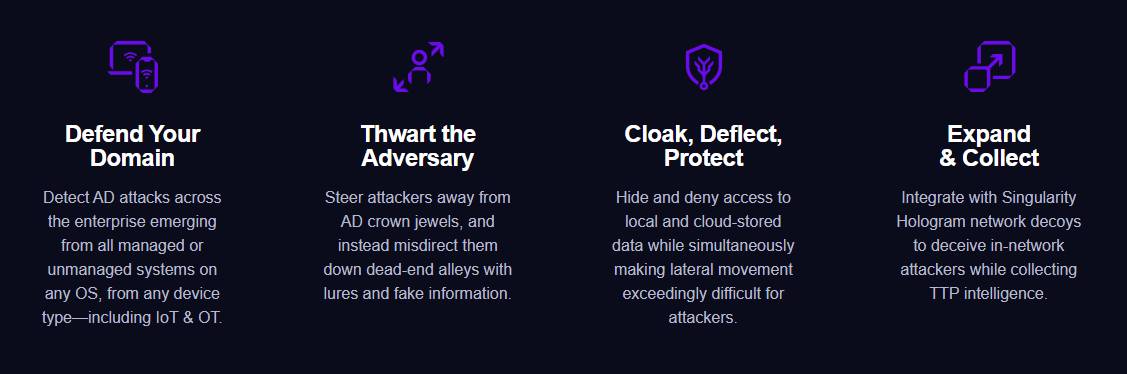
Defend Your Domain: A Comprehensive Approach

With Singularity Identity, organizations can detect Active Directory attacks across the enterprise, regardless of whether they originate from managed or unmanaged systems, running any operating system, including IoT and OT devices.
Thwart the Adversary: Misdirection and Deception

Steering attackers away from critical Active Directory components, Singularity Identity employs lures and fake information to misdirect them down dead-end paths, making their progress fruitless.
Cloak, Deflect, Protect: Safeguarding Access

This platform conceals and denies access to both local and cloud-stored data while simultaneously making lateral movement exceedingly difficult for attackers. It is a multi-faceted defense strategy.
Expand & Collect: Intelligence Integration
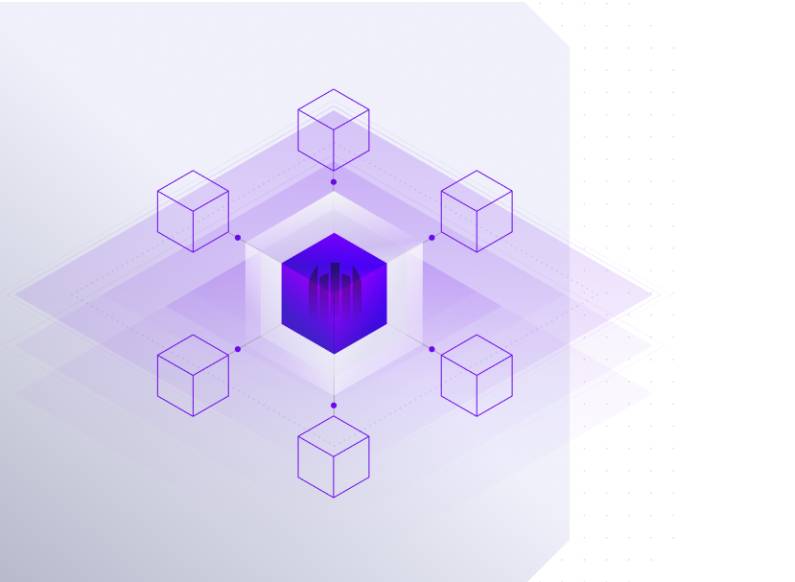
By integrating with the Singularity Hologram network decoys, Singularity Identity deceives in-network attackers while collecting Tactics, Techniques, and Procedures (TTP) intelligence.
Defend Identity at the Domain Controller: Robust Detection
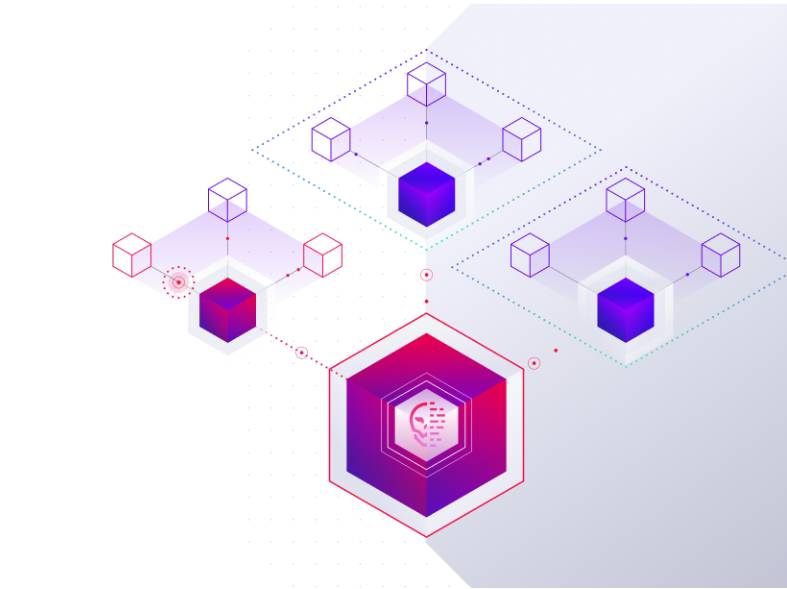
Singularity Identity detects identity attacks targeting Active Directory and Azure AD across the enterprise. It widens the net to include managed and unmanaged devices running any OS, providing high-fidelity, actionable information for directory asset defense.
Defend Identity at the Endpoint: Protecting Privileges
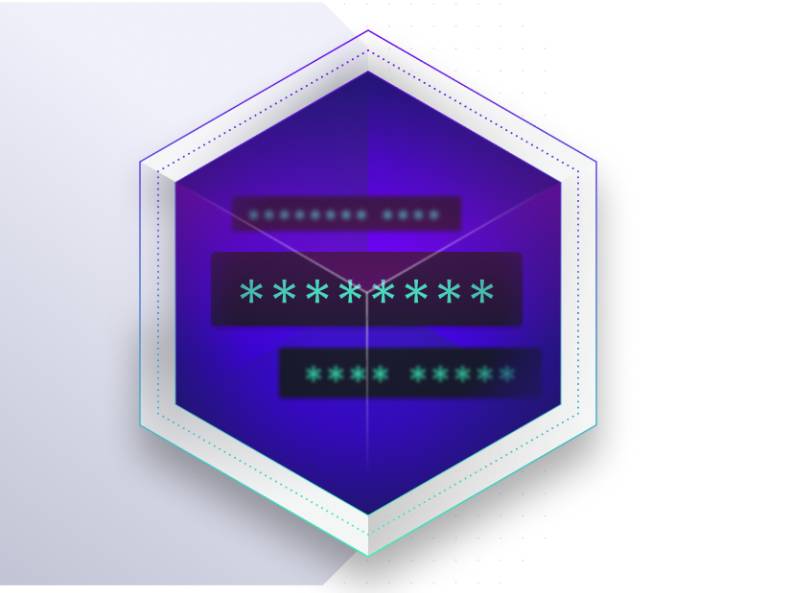
Gain visibility and awareness of attacker activity targeting critical domain servers. Protect privileged AD credentials from theft by replacing them with decoys. Identify service account compromises and access control misconfigurations.
Achieve Fast Time-to-Value: Streamlined Implementation
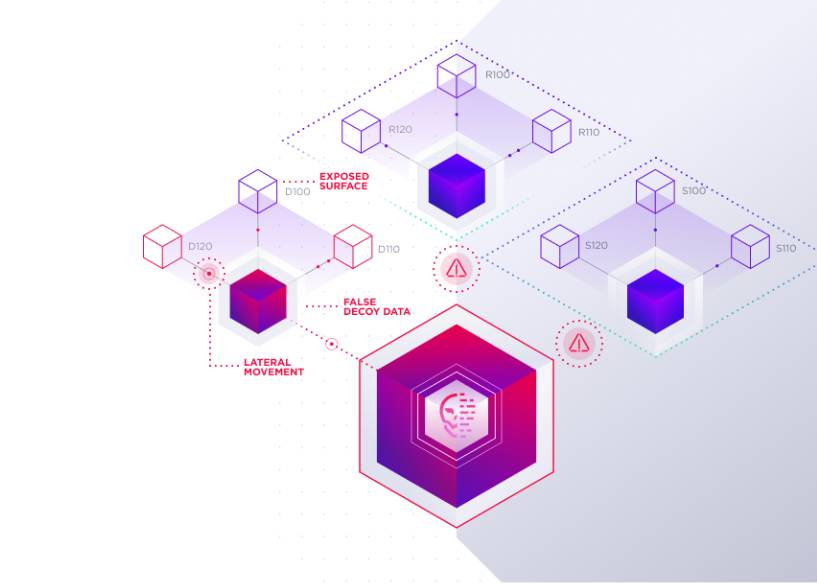
Singularity Identity offers easy implementation with low friction results. It can be flexibly deployed, including integration with Singularity Hologram for network decoy engagement and threat intelligence collection. It provides full coverage for on-premises Active Directory, Azure AD, and multi-cloud environments.
Support Your Zero Trust Program: Controlled Access Management
The platform helps limit implicit trust to applications and data resources, identifying identity exposures on endpoints, AD, and the cloud. It detects identity attacks and enforces access control to trusted applications within the user context.
Defend Production Data & Halt Lateral Movement: Cloaking Technology
Singularity Identity effectively slows adversarial advances with cloaking technology, stalls ransomware, and redirects attacker lateral movement traffic to network decoys.
Keep Credentials Safe: Prevent Misuse
The platform protects local application credential stores, halting credential harvesting and theft while feeding false credentials to lure attackers into revealing themselves.
Understand the Path to a Breach: Visual Insights
Singularity Identity helps organizations discover hidden elements throughout the network that enable lateral movement, offering topographical maps and insights to empower proactive defense strategies.
In conclusion, SentinelOne's Singularity Identity offers a comprehensive, proactive approach to Active Directory security. With its real-time defense capabilities, deception-based protections, and intelligence integration, it is a powerful ally in safeguarding identity assets and fortifying your organization against evolving cyber threats.
Related Posts
© 2025 Invastor. All Rights Reserved

User Comments